Troubleshooting Oracle / mk_oracle for Windows and Linux
In 2.2.0p24, the agent plugins mk_oracle, mk_oracle.ps1 and mk_oracle_crs are vulnerable to privilege escalation to root by the oracle user. With Werk 16232 we introduced a change that prevents privilege escalation to root.
Affected binaries are: sqlplus, tnsping and crsctl.
As a result:
- Windows
mk_oracle.ps1 - we now check if any non-admin users have Write, Modify or Full Control permissions on the affected binaries. . If such a user is found then the execution of the agent plugin is blocked and you will be notified about the non-admin user who owns the binary. - Linux
mk_oracle - If you use Oracle Wallet to connect to your Database and used the instructions of our official documentation to setup your configuration then you are also also affected by this change. Now, we have introduced a new functionality to the mk_oracle's “Just check the connection” mode ( -t ) so that it now also checks the permissions of the files. It will suggest you the desired permissions required on the ora files and the Oracle Wallet files.
ISSUE IMPACTS MK_ORACLE USERS USING CHECKMK 2.2.0P24. FIXED IN CHECKMK 2.2.0P25
Problem
All binaries, which are called by the plugins, are now checked if they need to be executed as a non-root (non-administrator under Windows) user, preventing the privilege escalation.
Affected binaries are:
- sqlplus
- tnsping
- crsctl
On Linux, this causes issues when using an oracle wallet as the unprivileged user might not be able to access the files defining the connection details and credentials which are primarily
- sqlnet.ora
- tnsnmaes.ora
- Oracle Wallet files
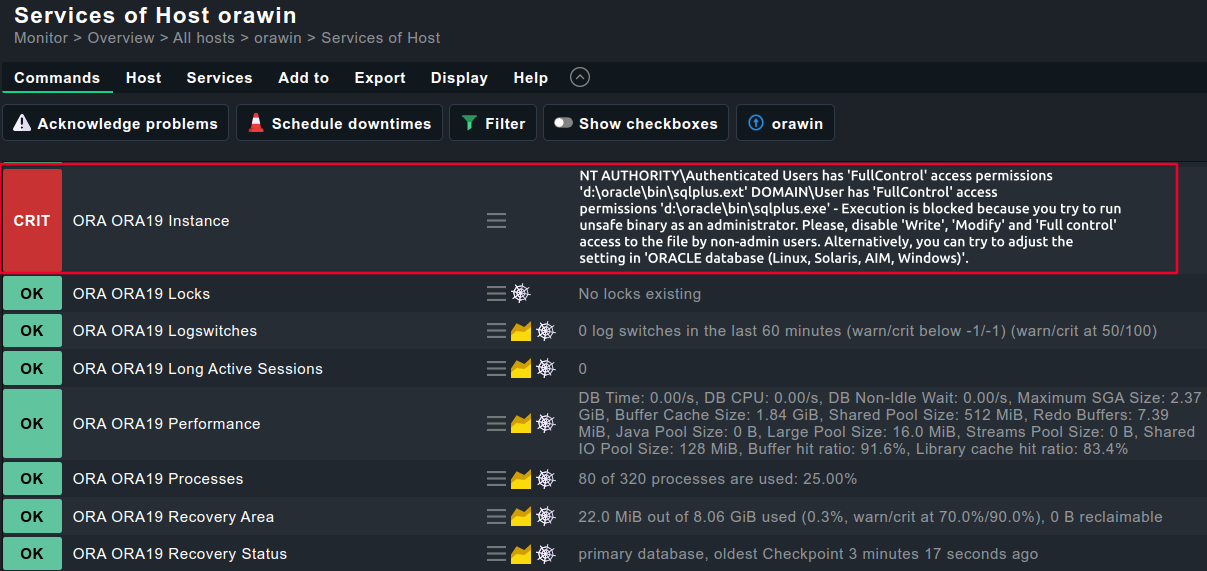
On Windows, the safe execution of the agent plugin is blocked because the non-admin users have either 'Write', 'Modify' or 'Full control' access to it. We recommend removing these permissions from the user/group who are shown as a member for these binaries.
Windows
If non-admin users have Write, Modify or Full Control permissions to the sqlplus binary, then executing the agent plugin with return an error with detailed description.
This is how the message may look like depending on which binaries the non-admin user has 'Write', 'Modify' and 'Full control' access:
Service check
Another error that could could happen is
This can be caused by:
- Non-supported setup like old tnsnames.ora in the configuration folder
- Modifying the agent plugin config files manually, and then the allowing the bakery to overwrite again
- An antivirus blocking the agent plugin
Agent output
<<<>>>
<<<oracle_instance>>>
<<<oracle_performance>>>
<<<oracle_processes>>>
<<<oracle_sessions>>>
<<<oracle_longactivesessions>>>
<<<oracle_logswitches>>>
<<<oracle_undostat>>>
<<<oracle_recovery_area>>>
<<<oracle_recovery_status>>>
<<<oracle_dataguard_stats>>>
<<<oracle_locks>>>
<<<oracle_tablespaces>>>
<<<oracle_rman>>>
<<<oracle_jobs>>>
<<<oracle_resumable>>>
<<<oracle_instance>>>
<<<oracle_processes>>>
<<<oracle_asm_diskgroup>>>
<<<oracle_instance:sep(124)>>>
ORA19|FAILURE|{Domain}\{User} has 'FullControl' access permissions 'd:\oracle\bin\tnsping.exe' - Execution is blocked because you try to run unsafe binary as an administrator.
Please, disable 'Write', 'Modify' and 'Full control' access to the the file by non-admin users. Alternatively, you can try to adjust settings in 'ORACLE databases (Linux, Solaris, AIX, Windows)'.
<<<>>>
Or
<<<>>> <<<oracle_instance>>> <<<oracle_performance>>> <<<oracle_processes>>> <<<oracle_sessions>>> <<<oracle_longactivesessions>>> <<<oracle_logswitches>>> <<<oracle_undostat>>> <<<oracle_recovery_area>>> <<<oracle_recovery_status>>> <<<oracle_dataguard_stats>>> <<<oracle_locks>>> <<<oracle_tablespaces>>> <<<oracle_rman>>> <<<oracle_jobs>>> <<<oracle_resumable>>> <<<oracle_instance>>> <<<oracle_processes>>> <<<oracle_asm_diskgroup>>> <<<oracle_instance:sep(124)>>> ORA19|FAILURE|NT AUTHORITY\Authenticated Users has 'FullControl' access permissions 'd:\oracle\bin\sqlplus.exe' - Execution is blocked because you try to run unsafe binary as an administrator. Please, disable 'Write', 'Modify' and 'Full control' access to the the file by non-admin users. Alternatively, you can try to adjust settings in 'ORACLE databases (Linux, Solaris, AIX, Windows)'. <<<>>>
Linux
We currently assume that the problems are caused by the Oracle user not being able to read all configuration files which it accesses to connect to the Database. As a result, you may get this error message from the agent plugin.
The oracle wallet, sqlnet.ora and tnsnames.ora must be readable for the oracle user (the oracle user also needs execute rights for the wallet folder).
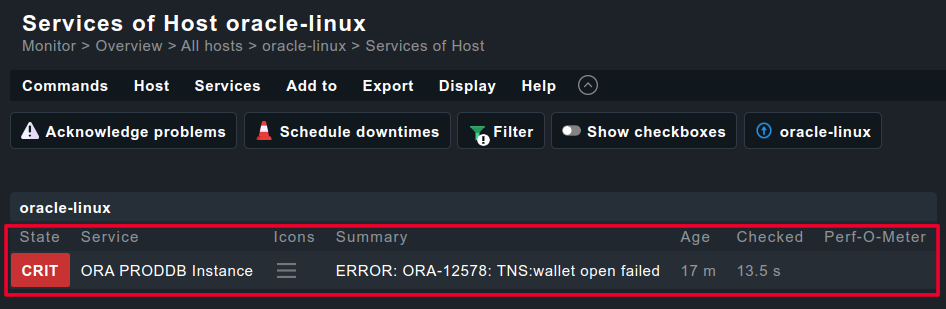
Service Check
sqlnet.ora
Oracle wallet
Agent output
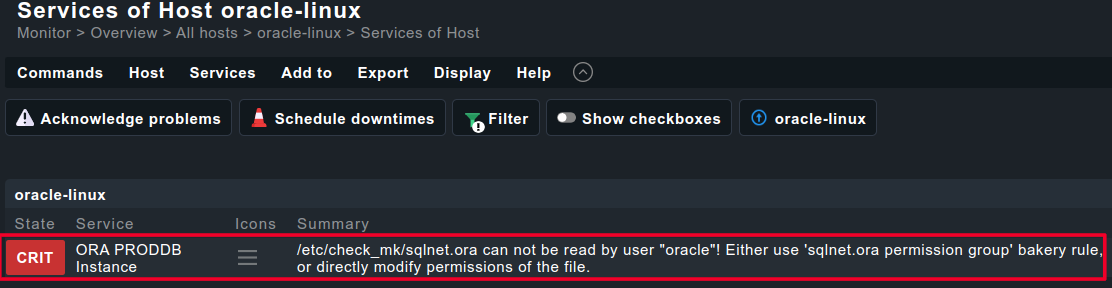
[root@linuxhost check_mk]# export MK_CONFDIR=/etc/check_mk/;export MK_VARDIR=/var/lib/check_mk_agent; /usr/lib/check_mk_agent/plugins/60/mk_oracle --no-spool <<<oracle_instance>>> <<<oracle_performance>>> <<<oracle_systemparameter>>> <<<oracle_processes>>> <<<oracle_sessions>>> <<<oracle_longactivesessions>>> <<<oracle_logswitches>>> <<<oracle_undostat>>> <<<oracle_recovery_area>>> <<<oracle_recovery_status>>> <<<oracle_dataguard_stats>>> <<<oracle_locks>>> <<<oracle_tablespaces>>> <<<oracle_rman>>> <<<oracle_jobs>>> <<<oracle_resumable>>> <<<oracle_instance>>> <<<oracle_processes>>> <<<oracle_asm_diskgroup>>> <<<oracle_instance:sep(124)>>> PRODDB|FAILURE|/etc/check_mk//sqlnet.ora can not be read by user "oracle"! Either use 'sqlnet.ora permission group' bakery rule, or directly modify permissions of the file.
Or
<<<oracle_jobs>>> <<<oracle_resumable>>> <<<oracle_locks>>> <<<oracle_instance>>> <<<oracle_processes>>> <<<oracle_asm_diskgroup>>> ERROR: ORA-12578: TNS:wallet open failed SP2-0640: Not connected SP2-0640: Not connected <<<oracle_instance:sep(124)>>> SP2-0640: Not connected <<<oracle_performance:sep(124)>>> SP2-0640: Not connected SP2-0640: Not connected SP2-0640: Not connected SP2-0640: Not connected SP2-0640: Not connected SP2-0640: Not connected <<<oracle_processes:sep(124)>>> SP2-0640: Not connected <<<oracle_sessions:sep(124)>>> SP2-0640: Not connected <<<oracle_longactivesessions:sep(124)>>> SP2-0640: Not connected SP2-0640: Not connected <<<oracle_logswitches:sep(124)>>> SP2-0640: Not connected <<<oracle_undostat:sep(124)>>> SP2-0640: Not connected <<<oracle_recovery_area:sep(124)>>> SP2-0640: Not connected <<<oracle_recovery_status:sep(124)>>> SP2-0640: Not connected <<<oracle_dataguard_stats:sep(124)>>> SP2-0640: Not connected <<<oracle_systemparameter:sep(124)>>> SP2-0640: Not connected
Solution
Windows
In mk_oracle.ps1(Windows) we now check if any non-admin users have Write, Modify or Full Control permissions on the affected binaries. If such a user is found then the execution of the agent plugin is blocked and you will be notified about the non-admin user who owns the binary.
You have the following possibilites:
- Please, disable 'Write', 'Modify' and 'Full control' access to the the Oracle binaries by non-admin users/groups ( The name of the user/group is listed in the error message in the agent output)
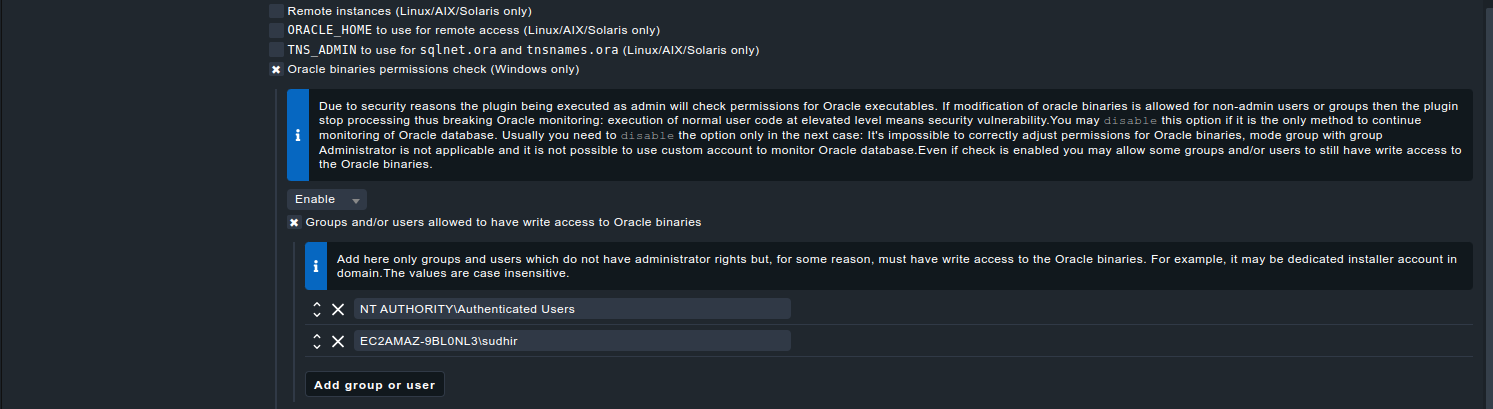
- If its impossible to correctly adjust the permissions for the Oracle binaries you can disable this permission check in the Oracle agent plugin rule under
- Go to Setup → Agents → Windows, Linux, Solaris, AIXAgent rules → ORACLE databases (Linux, Solaris, AIX, Windows)
Set it to Disable for the option "Oracle binaries permissions check (Windows Only)"
If you don't use the bakery then just add the following to C:\ProgramData\checkmk\agent\config\mk_oracle_cfg.ps1
C:\ProgramData\checkmk\agent\config\mk_oracle_cfg.ps1# Oracle plugin will not check if the used binaries are write-protected for non-admin users $SKIP_ORACLE_SECURITY_CHECK=1
If you don't want to disable the permission check but still allow the expected/specific users/groups to still have the elevated permissions you can configure it like this in the bakery:Without the bakery, its the following entry in C:\ProgramData\checkmk\agent\config\mk_oracle_cfg.ps1 :
C:\ProgramData\checkmk\agent\config\mk_oracle_cfg.ps1# Oracle plugin will allow users and groups in the list to have write access to the Oracle binaries $WINDOWS_SAFE_ENTRIES=@("NT AUTHORITY\Authenticated Users", "{Domain}\{User}")
- Go to Setup → Agents → Windows, Linux, Solaris, AIXAgent rules → ORACLE databases (Linux, Solaris, AIX, Windows)
Linux
In mk_oracle(Linux) : If you use Oracle Wallet to connect to your Database and used the instructions of our official documentation to setup your configuration then you are also also affected by this change. Now, we have introduced a new functionality to the mk_oracle's “Just check the connection” mode ( -t ) so that it now also checks the permissions of the files. It will suggest you the desired permissions required on the ora files and the Oracle Wallet files.
To make it a little easier, we expanded mk_oracle's “Just check the connection” mode ( -t ) so that it now also checks the permissions of the files. It will suggest you the desired permissions required on the ora files and the Oracle Wallet files.
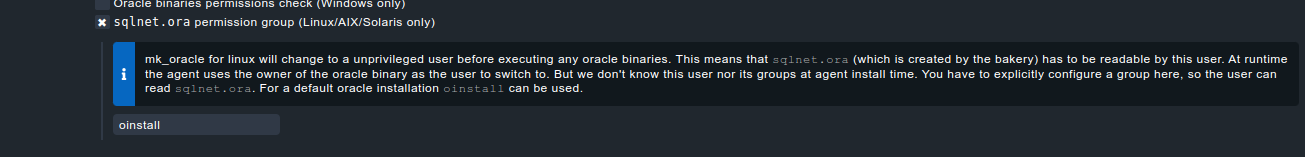
Regarding the sqlnet.ora, we also now have an option in the Oracle agent plugin bakery rule (Setup >> Agents >> Windows, Linux, Solaris, AIXAgent rules >> ORACLE databases (Linux, Solaris, AIX, Windows) with which its possible to configure the permission group of this file:
If you don't use the bakery, then you can run the following on the server where you have installed the agent:
[root@linuxhost check_mk]#chgrp oinstall "/etc/check_mk/sqlnet.ora" [root@linuxhost check_mk]#chmod g+r "/etc/check_mk/sqlnet.ora"
Below, you will find an example output from mk_oracle -t:
[root@linuxhost check_mk]# export MK_CONFDIR=/etc/check_mk/;export MK_VARDIR=/var/lib/check_mk_agent; /usr/lib/check_mk_agent/plugins/60/mk_oracle --no-spool -t
<<<oracle_instance>>>
<<<oracle_performance>>>
<<<oracle_systemparameter>>>
<<<oracle_processes>>>
<<<oracle_sessions>>>
<<<oracle_longactivesessions>>>
<<<oracle_logswitches>>>
<<<oracle_undostat>>>
<<<oracle_recovery_area>>>
<<<oracle_recovery_status>>>
<<<oracle_dataguard_stats>>>
<<<oracle_locks>>>
<<<oracle_tablespaces>>>
<<<oracle_rman>>>
<<<oracle_jobs>>>
<<<oracle_resumable>>>
<<<oracle_instance>>>
<<<oracle_processes>>>
<<<oracle_asm_diskgroup>>>
---checking permissions-------------------------------------------------
see https://checkmk.atlassian.net/wiki/spaces/KB/pages/70582273/Troubleshooting+mk+oracle+for+Windows+and+Linux
* sqlplus binary: /opt/oracle/product/19c/dbhome_1/bin/sqlplus
* sqlplus binary owner: oracle
* change user: true
* $TNS_ADMIN: /etc/check_mk/
* ERROR! user "oracle" can NOT read /etc/check_mk//sqlnet.ora
-rw-r-----. 1 root root 373 10. Apr 11:51 /etc/check_mk//sqlnet.ora
We suggest to change the group to oinstall and give read permission for the group:
chgrp oinstall "/etc/check_mk//sqlnet.ora"
chmod g+r "/etc/check_mk//sqlnet.ora"
If you use the AGENT BAKERY you have to use the rule 'sqlnet.ora premission group' to make this change permanently, otherwise it will be overwritten by an agent update.
* user "oracle" can read /etc/check_mk//tnsnames.ora
* test-login does not work!
Could not login. In case you are using a wallet to connect, there might be a permission error.
Make sure that the wallet folder can be read and executed by user "oracle" and
the files inside the wallet can be read by the user.
Consult your ora files for hints where the wallet is located:
/etc/check_mk//sqlnet.ora
/etc/check_mk//tnsnames.ora
------------------------------------------------------------------------
---login----------------------------------------------------------------
Operating System: Linux
ORACLE_HOME (oratab): /opt/oracle/product/19c/dbhome_1
Logincheck to Instance: proddb
Version:
<<<oracle_instance:sep(124)>>>
PRODDB|FAILURE|/etc/check_mk//sqlnet.ora can not be read by user "oracle"! Either use 'sqlnet.ora permission group' bakery rule, or directly modify permissions of the file.
SYNC_SECTIONS: instance performance systemparameter processes sessions longactivesessions logswitches undostat recovery_area recovery_status dataguard_stats locks
ASYNC_SECTIONS: tablespaces rman jobs resumable
------------------------------------------------------------------------
[root@linuxhost check_mk]# chown :oinstall sqlnet.ora
[root@linuxhost check_mk]# export MK_CONFDIR=/etc/check_mk/;export MK_VARDIR=/var/lib/check_mk_agent; /usr/lib/check_mk_agent/plugins/60/mk_oracle --no-spool -t
<<<oracle_instance>>>
<<<oracle_performance>>>
<<<oracle_systemparameter>>>
<<<oracle_processes>>>
<<<oracle_sessions>>>
<<<oracle_longactivesessions>>>
<<<oracle_logswitches>>>
<<<oracle_undostat>>>
<<<oracle_recovery_area>>>
<<<oracle_recovery_status>>>
<<<oracle_dataguard_stats>>>
<<<oracle_locks>>>
<<<oracle_tablespaces>>>
<<<oracle_rman>>>
<<<oracle_jobs>>>
<<<oracle_resumable>>>
<<<oracle_instance>>>
<<<oracle_processes>>>
<<<oracle_asm_diskgroup>>>
Logindetails: /@PRODDB
---checking permissions-------------------------------------------------
see https://checkmk.atlassian.net/wiki/spaces/KB/pages/70582273/Troubleshooting+mk+oracle+for+Windows+and+Linux
* sqlplus binary: /opt/oracle/product/19c/dbhome_1/bin/sqlplus
* sqlplus binary owner: oracle
* change user: true
* $TNS_ADMIN: /etc/check_mk/
* user "oracle" can read /etc/check_mk//sqlnet.ora
* user "oracle" can read /etc/check_mk//tnsnames.ora
* test-login does not work!
ORA-12578 suggests, that there is an error reading the wallet.
Detected sqlnet.ora as suggested in the documentation.
* ERROR! user "oracle" can NOT read /etc/check_mk/oracle_wallet
drwxr-x---. 2 root root 90 9. Apr 12:16 /etc/check_mk/oracle_wallet
We suggest to change the group to oinstall and give read permission for the group:
chgrp oinstall "/etc/check_mk/oracle_wallet"
chmod g+r "/etc/check_mk/oracle_wallet"
* ERROR! user "oracle" can NOT execute /etc/check_mk/oracle_wallet
drwxr-x---. 2 root root 90 9. Apr 12:16 /etc/check_mk/oracle_wallet
We suggest to change the group to oinstall and give execute permission for the group:
chgrp oinstall "/etc/check_mk/oracle_wallet"
chmod g+x "/etc/check_mk/oracle_wallet"
* ERROR! user "oracle" can NOT read /etc/check_mk/oracle_wallet/cwallet.sso
-rw-r-----. 1 root root 949 9. Apr 12:20 /etc/check_mk/oracle_wallet/cwallet.sso
We suggest to change the group to oinstall and give read permission for the group:
chgrp oinstall "/etc/check_mk/oracle_wallet/cwallet.sso"
chmod g+r "/etc/check_mk/oracle_wallet/cwallet.sso"
* ERROR! user "oracle" can NOT read /etc/check_mk/oracle_wallet/cwallet.sso.lck
-rw-r-----. 1 root root 0 9. Apr 12:16 /etc/check_mk/oracle_wallet/cwallet.sso.lck
We suggest to change the group to oinstall and give read permission for the group:
chgrp oinstall "/etc/check_mk/oracle_wallet/cwallet.sso.lck"
chmod g+r "/etc/check_mk/oracle_wallet/cwallet.sso.lck"
* ERROR! user "oracle" can NOT read /etc/check_mk/oracle_wallet/ewallet.p12
-rw-r-----. 1 root root 904 9. Apr 12:20 /etc/check_mk/oracle_wallet/ewallet.p12
We suggest to change the group to oinstall and give read permission for the group:
chgrp oinstall "/etc/check_mk/oracle_wallet/ewallet.p12"
chmod g+r "/etc/check_mk/oracle_wallet/ewallet.p12"
* ERROR! user "oracle" can NOT read /etc/check_mk/oracle_wallet/ewallet.p12.lck
-rw-r-----. 1 root root 0 9. Apr 12:16 /etc/check_mk/oracle_wallet/ewallet.p12.lck
We suggest to change the group to oinstall and give read permission for the group:
chgrp oinstall "/etc/check_mk/oracle_wallet/ewallet.p12.lck"
chmod g+r "/etc/check_mk/oracle_wallet/ewallet.p12.lck"
------------------------------------------------------------------------
---login----------------------------------------------------------------
Operating System: Linux
ORACLE_HOME (oratab): /opt/oracle/product/19c/dbhome_1
Logincheck to Instance: proddb
Version:
Error Message: PRODDB|FAILURE|ERROR: ORA-12578: TNS:wallet open failed
SYNC_SECTIONS: instance performance systemparameter processes sessions longactivesessions logswitches undostat recovery_area recovery_status dataguard_stats locks
ASYNC_SECTIONS: tablespaces rman jobs resumable
------------------------------------------------------------------------
The expected permissions are the following :
[root@linuxhost check_mk]# ls -l /etc/check_mk/*.ora -rw-r-----. 1 root oinstall 217 2. Apr 23:39 /etc/check_mk/sqlnet.ora -rw-r-----. 1 root oinstall 402 20. Feb 19:18 /etc/check_mk/tnsnames.ora [root@linuxhost check_mk]# ls -ld /etc/check_mk/oracle_wallet/ drwxr-x---. 2 root oinstall 90 2. Apr 23:35 /etc/check_mk/oracle_wallet/ [root@linuxhost check_mk]# ls -l /etc/check_mk/oracle_wallet/ total 8 -rw-r-----. 1 root oinstall 949 3. Apr 09:46 cwallet.sso -rw-------. 1 root root 0 2. Apr 23:35 cwallet.sso.lck -rw-r-----. 1 root oinstall 904 3. Apr 09:46 ewallet.p12 -rw-------. 1 root root 0 2. Apr 23:35 ewallet.p12.lck
Related articles

.png?version=1&modificationDate=1713538966296&cacheVersion=1&api=v2&width=1280&height=510)